Fluke Aircheck Wi-Fi Tester
Hello All,
I finally have got my hands on an Aircheck tester. I plan to use this device to locate rogue AP, do daily troubleshooting etc. I plan to share how to videos, cheatsheets etc to the wifi community for later reuse. I am not promoting the tools nor has Fluke networks reached out to me for this. Although it would be nice for them to give me a free tool since this content will help their product a lot :).
Lets dive right into it.
- Air check Quick start guide that comes with the tool
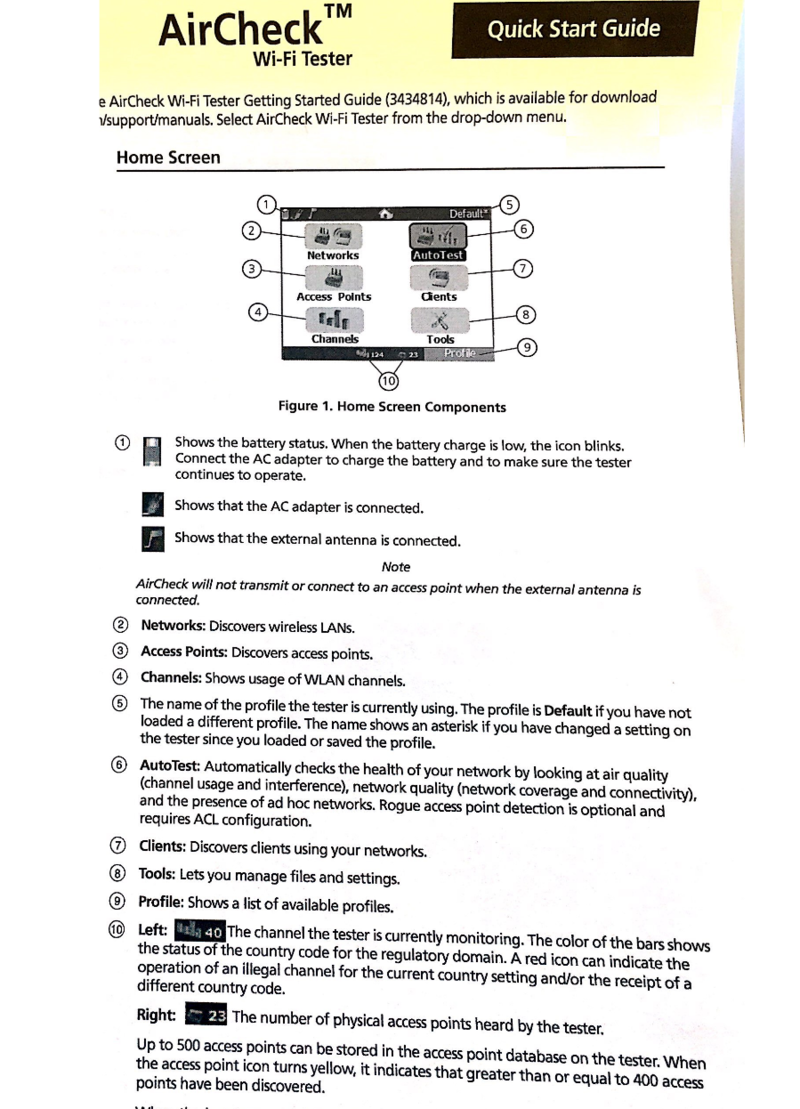
- Aircheck V3.0 Getting Started guide, Rev 5
(http://www.flukenetworks.com/findit/9829940)
- What’s in the box?

- Intro video to the ‘Networks’ tab on the home page
- Intro to the 'Access Points’ tab on the home page
- Intro to the ‘Channel Usage’ tab on the home page
- Creating a new network profile or editing existing one
- Bulk edit ACL using AirCheck Manager
The screenshot below show the AirCheck Manager interface. There are two main windows, one for on device info and other for locally saved info on the laptop
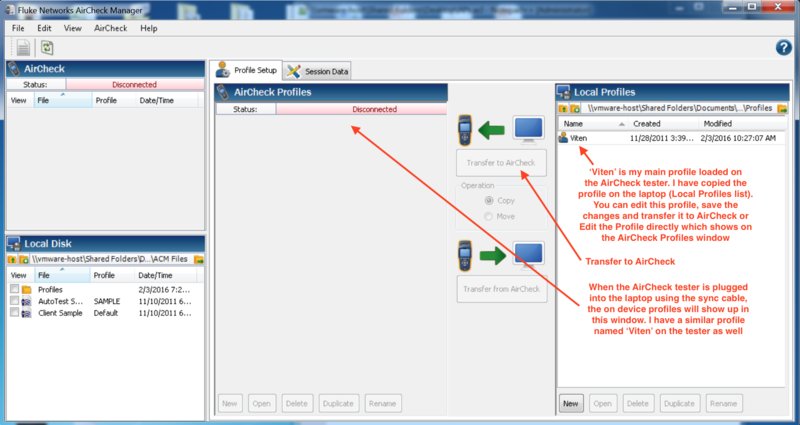
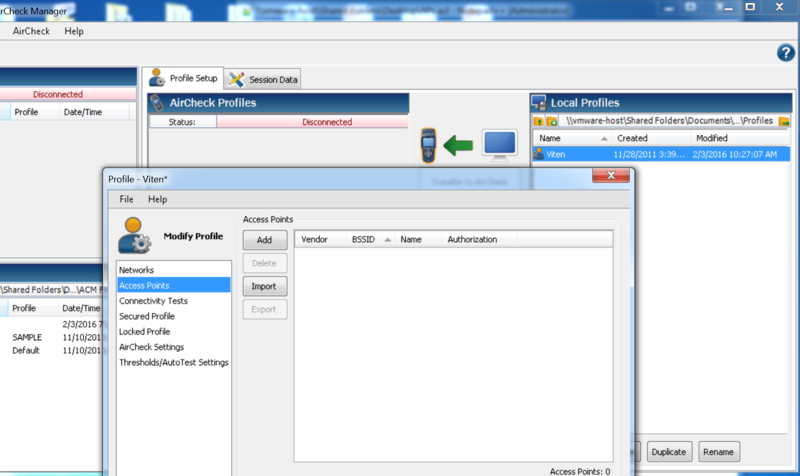
For editing the ACL using the manager, ‘open’ the profile which you want to edit. In this case i just have one profile called ‘Viten’. Once you open the profile, go to the Access Point tab
Now, just click on the ‘Add’ button 2-3 times to create some dummy BSSID’s like below
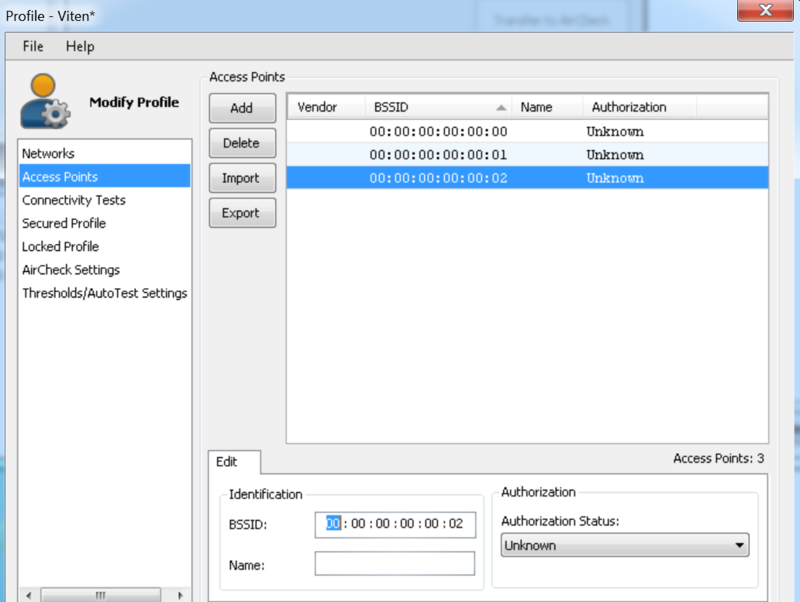
Next export this list. The file extension will be *.acl. You can open this file using a text editor like notepad++. The list layout is simple column separated. Now if you have a list of BSSIDs of your corporate or known Access Points (you can get the list from a saved session on the wifi tester itself, or export it from the WLC or Cisco Prime). You can mark all the known BSSID as ‘authorized’ in the .acl file as shown below
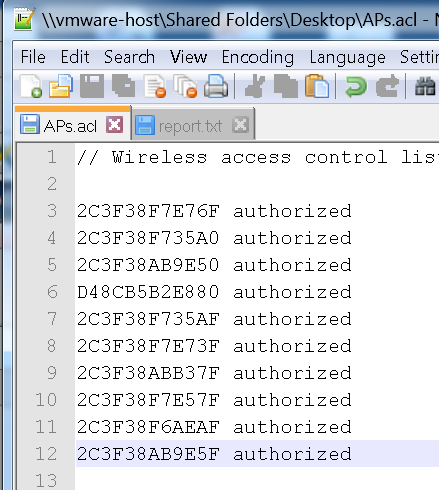
Save the file and reimport it back to the Access Point tab on the profile page. Done!! you have now marked all the trusted APs as ‘authorized’. The video below shows the updated profile on AirCheck tester with a authorized sign against the APs broadcasting the SSID ‘blizzard’ in my case. The rest of the BSSID are still tagged as ‘unauthorized’ since that is my default tagging.
- Connecting to an AP using the created network profile and running ping test
Part 1, Fluke tester failing authentication
Part 2, connection successful and ping test