The next document briefly explains how to creat an internal PKI for lab purposes, using last-call server.
You will learn how to:
- Create a root CA
- Create a CSR for your WLC (webauth admin)
- Sign a CSR to generate a certificate
- Chain the certificate
- Install the certificate on your WLC
- Confirm the certificate is installed correctly
- Confirm the certificate is valid
- Verify which root CAs certificates are installed on your machine
- Install the CA's certificate on your machine
Prerequisites
This document assumes that you have a basic understanding of the next concepts:
- PKI (Public Key Infrastructure)
- CA (Certification Authority)
- CSR (Certificate Signing Request)
- Certificate
Requirements
Create a root CA
We will create a directory where we will save our PKI stuff
***Parts in orange are the things that you can customize
2- Check the directory where you are in this moment
3- Create the directory where you will save your PKI stuff
# mkdir name-of-directory
4- Move to that directory
5- Create the key for your root CA
# openssl genrsa -out CA's-key.key 2048
6- Create the root CA's certificate
# openssl req -x509 -new -nodes -key CA's-key.key -days 1000 -out CA's-cert.pem
7- Confirm your CA cert and your CA key where successfully created
Create a CSR for your WLC
This step may done from your PC, using openssl, or you can do it also from last-call. If you were a customer, you would be do it on your PC.
# openssl req -newkey rsa:2048 -nodes -keyout device's-name-key.pem -out device's-CSR-name.pem
Confirm you created WLC's CSR and key
# ls -l
Use your root CA to sign the WLC's CSR
***If you were a customer, you would have to send your CSR to somebody (usually the system administration or the security guy) to sign it, and then they would send you back the certificate (in this example, they would send back WLC-cert.crt)
# openssl x509 -req -in device's-CSR-name.pem -CA CA's-cert.pem -CAkey CA's-key.key -CAcreateserial -out WLC-cert-signed.crt -days 1000
Confirm it was generated
# ls -l
Chain your certificate
***If you were a customer, you woul need to ask to the system administrator to provide the root CA's certificate, to be able to make this step, in our example, as we are also the sytem administrator, we are able to do it by ourselves.
1- Open your WLC's cert
# more WLC-cert-signed.crt
copy the content and paste it into a notepad
2 - Open your root CA's cert and copy it in the same notepad just right after the device cert
#more CA's-cert.pem
3- Create a new file called All-certs.pem
4- Copy the content of the notepad and put it in All-certs.pem. To do so:
- select all the text on the notepad and copy it.
- left click on the screen that was opened after typing "vi All-certs.pem"
- type the letter "i" on your keyboard
- righ click on the screen that was opened after typing "vi All-certs.pem"
- the text should be copied on All-certs.pem screen
If you notice that there are some missing characters, you can add them manually. To do so, please:
- Type ESC
- move with the cursor to the location where you need to start typing
- type "i" letter
- start typing the missing characters
- when you are done, type ESC
- Shift + q
at the end of the file, will appear ":"
-then write "wq!" and hit enter
To confirm it was created right, open it
# more All-certs.pem
5- Put together All-certs.pem with the device's key
# openssl pkcs12 -in All-certs.pem -inkey device's-name-key.pem -out All-certs.p12 -clcerts -passin pass:cisco123 -passout pass:cisco123
# openssl pkcs12 -in All-certs.p12 -out final-cert.pem -passin pass:cisco123 -passout pass:cisco123
# ls -l | grep final-cert
Install the certificate on your WLC
To store the final-cert.pem on your PC, you can simply copy and paste it to a text file and change the extention to .pem.
Make sure your certificate looks similar like this:
Download it to your WLC.
>transfer download filename final-cert.pem
>transfer download datatype webadmincert
>transfer download serverip 10.10.10.10
>transfer download mode tftp
>transfer download certpassword cisco123
>transfer download start
Confirm the certificate is installed correctly
From the GUI, go to MANAGEMENT > HTTP-HTTPS
Reboot the WLC to enable it
>save config
>reset system
Confirm the certificate is valid
1- Login by https to your WLC 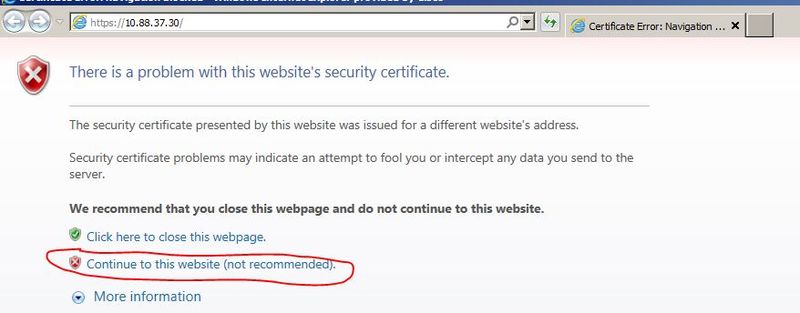
2- Open the error message about the certificate 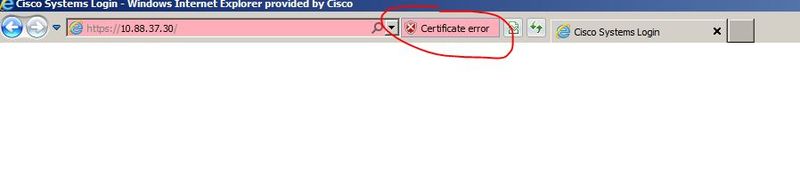
3- Check the certificate that is being used by the WLC
4- We can see that the certificate is not valid because the field "Issued to" does not match with the data on the address bar
5- As I dont currently have a DNS server, I will add manually WLC-kcg to be resolved to 10.88.37.30 on my PC.
- On you PC go to C:\Windows\System32\Drivers\etc and open "host"
- Add the hostname and the IP to which it should be translated
- Save and close "hosts" file
6- Close and open again your browser, now pointing to the hostname
7- Review why still unvalid :(
8- It seems that the root CA that signed our cert is not trusted by our PC.
Verify which root CAs certificates are installed on your machine
We can verify which root CAs are trusted by our PC by going to
- Win + R
The root CA that signed our cert should be listed here, otherwise, our laptop wont trust it. As rootCA-kcg is not listed here, thats why we receive the error.
Install the CA's certificate on your machine
You can copy the root CA certificate that was created on last-call and save it to your PC on a txt file, and then change the extention to .crt
- Double click it and install it
Verify again which root CAs are trusted by our PC by going to
- Win + R
Close and open again your browser, pointing to the hostname and feel happy that finally the certificate is valid
if you want to verify again the certificate used by the portal:
































